The way businesses work has changed, and network security needs to keep up. Traditional security methods – things like VPNs or perimeter firewalls – simply aren’t designed for the way companies operate now. We’re talking about remote teams, cloud-first tools, and flexible devices used from just about anywhere.
That’s where the Software Defined Perimeter (SDP) comes into play. It’s a smarter approach to secure access, and when paired with a solution like Remote WorkForce ZTNA, it becomes even more powerful.
What Exactly Is a Software Defined Perimeter?
Think of SDP as making your systems invisible to the outside world. Instead of having open doors with guards, you hide the building altogether. Services stay concealed until the right user comes along with the proper ID and device. Only then does access become available.
The idea came from the defence sector, and it’s since evolved to support modern digital infrastructure. Instead of trusting anything by default, SDP works by validating every attempt to connect – not just based on a login, but on the health of the device, the user’s identity, and the context of the request.
Key concepts include:
- Verifying both user identity and device posture before allowing access
- Keeping all internal services hidden until authentication is confirmed
- Granting access only to the specific resource needed – not the entire network
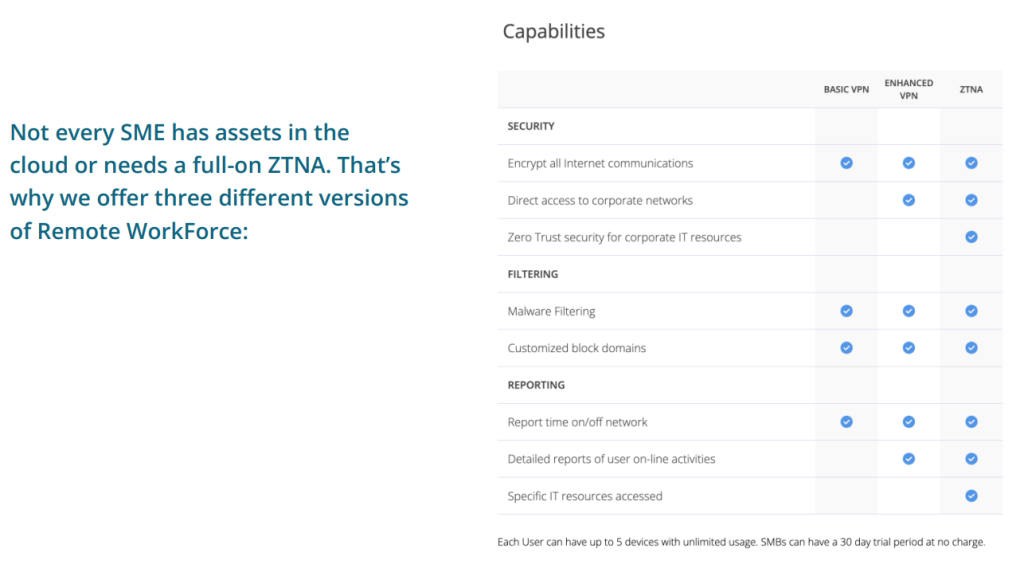
SDP vs VPN vs ZTNA: What’s the Real Difference?
| Feature | VPN | SDP | ZTNA (Remote WorkForce) |
|---|---|---|---|
| Network Exposure | Broad access once connected | Services hidden by default | App-specific visibility |
| Verification Model | One-time login | Identity and device checks | Identity, device, and context |
| Setup Complexity | Often hardware-heavy | Can be technical to configure | Lightweight, deploys fast |
| Flexibility | Limited cloud or remote support | Moderate flexibility | Built for hybrid environments |
| Access Control | Network-wide access | Application-level segmentation | Dynamic, policy-based access |
While SDP and ZTNA both aim for the same goal – securing access based on trust and identity – ZTNA is more flexible and often simpler to manage. That’s especially true when using Remote WorkForce ZTNA, which builds on SDP ideas but removes the technical hurdles.
Why Remote WorkForce ZTNA Works Better Than Traditional SDP
There are plenty of tools that follow the SDP model, but many are designed for large enterprises with deep technical teams. For small and mid-sized businesses, that kind of complexity can be more of a burden than a benefit.
Remote WorkForce ZTNA cuts through that with an approach that’s practical and effective:
- Access stays invisible until approved
No exposed ports or services – users only see what they’re meant to see. - Quick and clean deployment
No specialised appliances or weeks of planning – most setups are done in hours, not days. - Role-based and device-aware
Access is tied to both who the user is and what device they’re using – all checked in real time. - Simple to manage
A central dashboard gives you a clear view of user activity, with intuitive tools to control access. - Optimised for cloud and BYOD
Whether your apps are in the cloud or your staff are using personal devices, access stays secure.
Enforcing the Principle of Least Privilege
Good security means giving people only what they need. Anything more opens the door to mistakes or worse, breaches. But in traditional networks, once someone’s in, they can often roam further than they should.
Remote WorkForce ZTNA applies least privilege by default. Each person’s access is defined by who they are, their device’s condition, and what their role requires. Change any of those factors, and their access adjusts too.
This isn’t just efficient – it helps reduce human error and limits the blast radius if something ever goes wrong.
Why SMEs Benefit Most from Reducing Their Attack Surface
For small businesses, security often means making smart decisions with limited resources. Unfortunately, traditional VPNs and exposed services often offer too much visibility to attackers. Hackers only need one open port or forgotten service to get a foothold.
Remote WorkForce ZTNA addresses this by:
- Keeping everything hidden by default
- Blocking unauthorised connection attempts before they even start
- Using layered checks that make spoofing or guessing nearly impossible
With fewer visible entry points, the odds of being targeted drop dramatically – and that’s the sort of quiet confidence SMEs need in their corner.
Supporting BYOD Without Opening Security Holes
Personal devices can boost productivity, but they’re a challenge when it comes to keeping networks secure. Not every laptop or phone is up-to-date or protected properly.
That’s why Remote WorkForce ZTNA checks each device before allowing access. It verifies:
- Whether the operating system is secure
- If recent patches and updates are applied
- Whether the device meets internal security rules
Devices that don’t measure up get restricted access – or none at all. So businesses can support remote work and personal hardware without compromising on safety.
Making the Shift to ZTNA Seamless
You don’t need to flip a switch overnight. Transitioning from traditional access methods to ZTNA can be done in stages, starting with a single app or team and expanding from there.
Here’s a typical approach:
- Identify high-risk systems that need stronger controls
- Deploy Remote WorkForce ZTNA for those users first
- Monitor usage and gather feedback
- Extend to other services as you refine your access policies
- Phase out legacy VPNs over time
This phased rollout reduces disruption while steadily improving your security position.
The idea behind a Software Defined Perimeter is sound: only let in who you trust, and make the rest invisible. But not every business needs a complex enterprise-grade solution to do that.
Remote WorkForce ZTNA delivers the benefits of SDP in a way that makes sense for modern businesses. It’s secure, simple, and scalable – without the baggage of legacy tools or complicated systems.
If you’re looking to modernise your access strategy, this is a practical step in the right direction.
Contact our experts today to discuss Private Communications Corp Solutions
👉 https://exertisenterprise.com/private-communications-corp/